The news media are breathlessly scaring the hell out of everybody lately, warning us of impending doom that awaits us from WannaCry, the latest in a series of ransomware viruses.
Where did this modern scourge of civilization as we know it come from, for goodness’ sake? Uh….a leak from the NSA, sometimes known as Nobody’s Safe Anymore. They have an inventory of hidden vulnerabilities in Windows they choose not to pass on to Microsoft so they can be addressed. Never know when they might come in handy for super secret government work, you know.
Despite all the hysterical media talk, WannaCry is not a “worm”. A worm is an attack on your router. WannaCry is a virus, and you get it from email attachments and poisoned links in email. You don’t “catch it” from toilet seats, either. You trigger it yourself.
By the time you see the ransomware demand screen, it’s already too late. Brace yourself for a really bad day. You’re screwed. Any attached backup drive is also screwed, and so are those “safe files” you have secreted on DropBox, GoogleDrive or Microsoft’s OneDrive. As soon as these files are corrupted on your local machine, they’re synchronized with your cloud storage files.
I had a consulting client attacked last fall with an earlier version of WannaCry, called Zepto, and it wiped out a large public self-storage business. See story below. Their database, email, documents, photos, and their backup drive got completely encrypted. The only thing that didn’t get wiped out was Windows itself, which the virus left unperturbed. Purely by luck, other machines on the network were unaffected in this case, possibly because we immediately hit the power switch on all connected machines before it spread. I don’t know if WannaCry behaves the same way, and I don’t want to find out.
Recovery started with disconnecting the infected machine from the network and removing the active part of the virus. Zepto renames encrypted user files as *.zepto. User files were completely unrecoverable, and they were deleted from a DOS prompt with:
“c:\del *.zepto /s”.
You might as well delete them, because you’ll never see their unencrypted contents again. Unfortunately, this machine was used as a peer-to-peer “server” for a critical shared app. It was toast.
Ultimately, I reformatted the machine, brought the Windows updates current and reinstalled everything. It’s the only way you can be sure. Then I reinstalled the user’s management software they used to run the business. The only thing that saved us was an old off-line backup drive we had replaced six months earlier. That meant six months of daily transactions had to be manually reentered, which took a month, but they were eventually able to get back to normal operations.
I’m suggesting to my clients that they take this virus very seriously.
- The key word is “off-line”. Buy a second removable hard drive and swap them out after their (usually weekly) backups complete, with only one drive attached at any time. Do it nightly if you’re fastidious or have mission critical files to worry about, such as a medical facility, but most people do it weekly. Another alternative, if you have the chops to do it, is to use drive imaging software to clone your drive, and then disconnect the drive. Then it’s just a drive swap to get back in business. But bottom line, any user files you can see in Windows Explorer are going to get destroyed.
- Make certain that everybody understands what to do if a machine gets infected: hit the power switch on the now wasted machine and shut down every machine on the network immediately. At the same time, pull the power plug out of the router and any network switches. Minutes count.
- This virus uses email as an attack vector. This client had been receiving daily emails for weeks, all short, plausible messages designed to trick the unwary into clicking on an email link or to open an attachment. “Your contract is approved and needs your signature”, “Your credit card was declined. See attached.”, or simply “See invoice attached.” Finally, Bad Luck Brian (there’s one in every office) clicked on an attachment, “because I wanted to make sure it wasn’t deleting something important”, and the game was afoot. It is critically important that every person in your office understands what to watch for and to delete such messages without opening the attachments or following links in messages. It may or may not appear to be from someone you know.
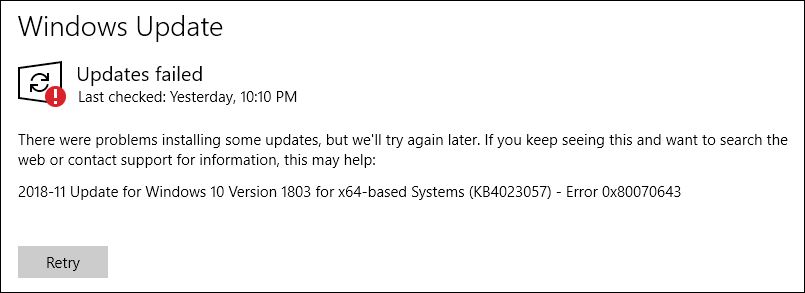
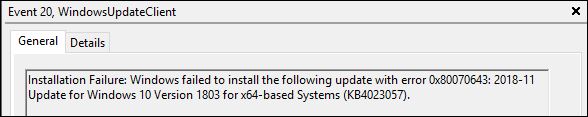
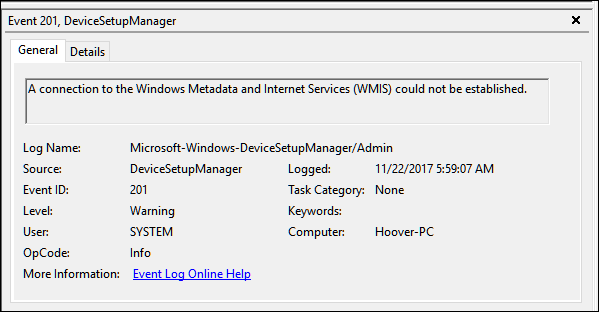
- The most likely victims of WannaCry are older systems not running Windows 10 or systems that are not current with Windows Updates. Sometimes it’s because updates upset older software, but more often than not, Windows Update itself has gotten stuck. Many businesses depend on old or poorly designed software that will not run on Windows 7 or Windows 10. Some lazy or incompetent vendors even require you to lower your security settings in order to run at all, even under Windows 10. I currently have two such clients, so it’s not as rare as you might think. Might as well put “Kick Me” signs on them. Many process control systems, including hospitals, traffic signals and ATM machines still rely on Windows XP, believe it or not.
In the end, an off-line backup is your best protection.